1: Search engines
Using a search engine is more than typing in the address, putting a couple of keywords into the big text box, clicking Search, and choosing the first result. While that may work, it won’t give you the best results much of the time. Learning the advanced search, Boolean operators, and how to discern good results from bad results goes a long way toward enabling you to use a computer as a powerful research tool.
2: Word processing
Word processing is one of the oldest uses for a computer. And it continues to be extremely important, even though in many ways its functions have been put into other applications. (For example, people may write more emails than documents, but the task is nearly identical.) It is tough to claim to be computer literate if the basic functions of word processing like spell check, table creation, and working with headers are outside your capabilities.
3: Spreadsheets
Spreadsheets were the killer application that got a lot of people willing to pony up big bucks for a PC in the early 1980s. Spreadsheets offer incredibly powerful analysis possibilities… if you know how to use them for more than storing the holiday card address list. (Okay, I use Excel for that too.) Being able to use formulas, references, and macros can turn a “grid of numbers” into actionable information in the hands of the right person.
4: Browser basics
It is almost painful to watch some “computer savvy” people operate a Web browser. The most obvious goof is going to a search engine to type in the address of the site they want to go to. But folks are unaware of a lot of other things they do that make the Internet more difficult than it needs to be. Mastering techniques like opening links in new windows, using bookmarks, editing URLs to perform navigation, clearing the browser cache, and understanding common error messages will give you access to a world of unlimited information instead of keeping you stuck with only what Web site designers make obvious.
5: Virus/malware scanning
Much of typical computer maintenance is automated or unneeded at this point, but it is still essential to understand how to check a system for nasty bugs, spyware, and other malicious applications. While the scanning tools come with real time monitors, something can still slip onto the system before the scanner has the right filter for it. So it’s critical to know how to trigger a manual virus/malware scan, as well as how to use alternative systems, spot signs of an infection, and other similar tasks.
6: Common keyboard commands
If you do not know how to copy/paste without a mouse, you are not computer literate. Sorry! Every operating system has some universal keyboard commands, and while knowing them won’t add 30 minutes back into your day, it will take a lot of the “friction” out of using a computer. Learning these commands is more a matter of routine than anything else; a short tutorial done once a day for a week will probably be enough to put you in the habit, and it will make you a happier user.
7: Basic hardware terminology
It is tough to have someone help you with a problem when you tell them that your “hard drive” is unplugged, when you really mean “the computer.” There are a number of common hardware misunderstandings out there, and while some are understandable (for instance, confusing a NIC with a modem the cables look similar and they serve the same purpose, networking), knowing basic hardware terminology is a must-have skill to be a savvy user.
8: Simple networking diagnosis
Networking problems create the most common trouble with most computers. While you don’t need to be able to program a Cisco router, you should know how to:
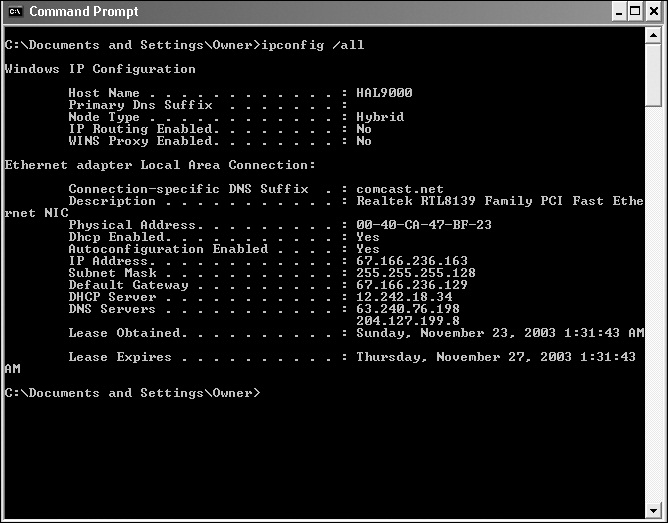
Determine your IP address
Verify physical connectivity to the network
Check that you have a logical connection to the network
Find out what path network traffic takes to get to its destination
Translate from DNS names to IP addresses
9: How to hook it up
Despite the color coding of connections and the fact that most cords can be plugged into only one hole, tons of people still can’t hook up a computer. It is tough to claim to be computer literate if you can’t even get it hooked up and turned on without some help.
10: Security/privacy 101
It is a dangerous world out there! You absolutely must know how to protect yourself from attackers on the Internet and keep your personal data private. Everything from knowing to check a link before you click it to verifying that encryption is being used to transmit sensitive data to researching sites before giving them your personal data are all critical skills for the modern computer user. If you do not know how to keep yourself safe, you need to learn how.